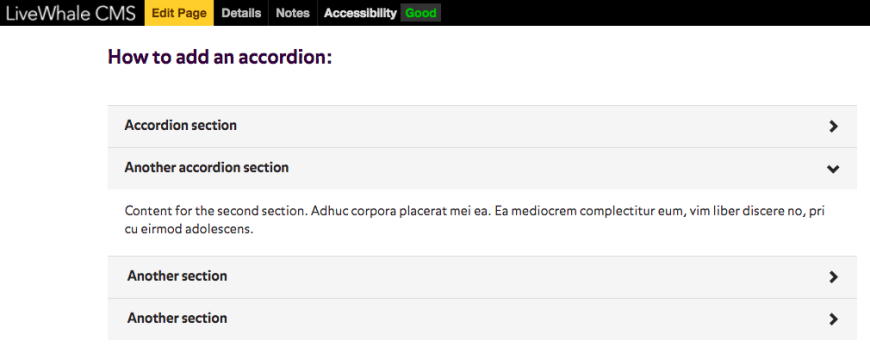
Accordions
Accordions allow you to display multiple sections of content in a concise layout. As the name indicates, it expands like an accordion. When you first load it, only the section headings are visible, with the “>” symbol appearing next to each section heading. Pressing the “>” expands that section, opening the accordion.
Accordions makes each section easy to find without scrolling down a long page of text.
The following example shows an accordion in both states – the first is closed, and the second is open - and showing its content. When in an “open” state, the “down arrow” can be used to close that section.
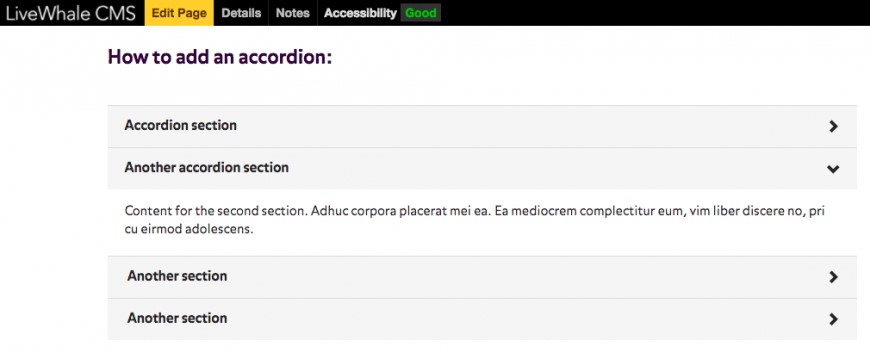
Accordions are built using a single-column table, with a pair of rows per entry – one row for the heading, and a second row for the content.
Accessibility Tip: Tables are difficult to navigate - and must be carefully labelled with meaningful row and column headers.
Accordion Examples
Example of a working accordion, this table has an even number of rows (four total):
| Confidentiality Information Policy |
|
Purchase College is committed to protecting the privacy and confidentiality of information contained in the multiple databases and print files maintained by the college in the regular course of business. Personal information that is confidential in nature will be used only in accordance with Purchase College Information Security Program, Family Educational Rights and Privacy Act (FERPA), Health Insurance Portability and Accountability Act (HIPAA) regulations, and all applicable SUNY, state, and federal regulations. POLICY Employees at Purchase College by nature of their positions will gain access to private personal information about students, faculty, staff, alumni, and other constituents of the college. Employees are obligated to maintain the confidentiality of any such private personal information that is encountered. Purchase College expects all employees with access to personal information to deal with that information in a respectful and professional manner. As a matter of policy, the college restricts access to personal information to only those employees who have a legitimate “job-related reason” in the performance of their duties for gaining access. Access and release of any student educational records must be in accordance with FERPA regulations. Access and release of any health records must be in accordance with HIPAA regulations. Any personal information viewed or accessed by an employee through college systems or records is not to be shared or released to others unless there is a legally permissible purpose for doing so. In addition, in accordance with Section 203-d of the New York Labor Law, Purchase College will not:
Personal Identifying information (PII) is defined by NYS as including an employee’s Social Security number, financial account number and PIN, or driver’s license number. Access to PII will be restricted to those with a demonstrable need for access. Inappropriate disclosure of information pertaining to students, faculty, staff, and other college constituents may violate applicable law and is considered a violation of ethics and a breach of trust placed in employees by the college. Upon finding of a breach of this policy by an employee in a collective bargaining unit, the college may initiate disciplinary action pursuant to the applicable collective bargaining agreement, up to and including termination of employment. Employees who deal with confidential material on a regular basis will be required to sign a confidentiality statement and to complete annual information security training. Each campus manager will determine employees required to have access to PII who must receive training and sign confidentiality statements. GUIDELINES Employee, student, financial, and medical information contained within Purchase College information systems (electronic and physical files) and external SUNY systems is considered confidential. Access to information made confidential by law or campus practice is limited to those individuals (employees, consultants, adjunct professors, third-party vendors, etc.) whose position legitimately requires use of this information. The employees (Purchase College faculty, staff, student employees, and volunteers appointed by the college) understand that by virtue of their work for Purchase College they may have access to data that are confidential, and therefore understand they may not disclose such confidential data to any person or entity without appropriate authorization, subpoena, or court order. Examples of confidential PII information include the following:
In addition, FERPA regulations cover
In order to access confidential information, employees agree to adhere to the following guidelines:
PROCEDURES
|
| Digital Millennium Copyright Act (DMCA) Policy |
|
As a community of artists, writers, musicians, filmmakers, and scholars whose careers will be spent creating intellectual property, we encourage our entire community to respect the property of others. Downloading anything onto your machine from untrustworthy P2P (peer-to-peer) sources or websites not only exposes you to viruses, worms, and spyware, but often violates the copyright laws and can lead to suspension of network privileges, or to lawsuits from the Recording Industry Association of America (RIAA), the Motion Picture Association of America (MPAA), or the Business Software Alliance (BSA). Please remember that theft is a crime, and that nothing in cyberspace is truly anonymous. Copyright protections are created when words are put on paper, transmitted via email, when music is recorded, software is written, or when an image is created. Once done, the work is protected by copyright—no formal copyright registration or seal is required for copyright protection to be in effect. If someone else wants to use the work, they must get permission from its creator. Copyrighted material includes almost all forms of original expression fixed in tangible medium even if no formal copyright notice is filed or attached. However, you cannot copyright any idea, process, system, method of operation, concept or principle, regardless of the form in which it is described. Copyright infringement is any reproduction (download), display, distribution (upload), creation of derivative works, or public performance of copyrighted work without permission of the copyright owner. Federal copyright law and college policy prohibit the copying and/or distribution of copyrighted material without the permission of the copyright owner. Copyrighted materials include but are not limited to text, graphics, art, photographs, music, film, and software. Peer-to-peer (P2P) software such as BitTorrent that is often used to share music, movies and other media may lead to violation of copyright laws. Most P2P software automatically shares anything that you download by default—so if you downloaded the latest Hollywood blockbuster to watch it, you would also be helping to distribute an illegal copy to others by sharing the contents of your machine with the world. If you use any P2P software for legitimate purposes, as a security precaution, you should disable its file sharing component. There is an IU website with details on disabling file-sharing for most P2P software: http://protect.iu.edu Digital Millennium Copyright Act (DMCA) The DMCA can be reviewed at: http://www.copyright.gov/legislation/dmca.pdf An overview of the act can be found at: http://www.arl.org/focus-areas/copyright-ip To report alleged copyright infringements on Purchase College computers, please contact the college’s designated DMCA agent:
Bill Junor
Pursuant to the provisions of the Digital Millennium Copyright Act, Purchase College receives DMCA Copyright Infringement Notices alleging that computer(s) registered to Purchase College IP addresses are allegedly illegally infringing on copyrighted materials belonging to others. Infringement of copyright is a violation of Federal law, and the violator is subject to both substantial fines and civil damages. Under the DMCA, as an Internet Service Provider (ISP), the college is obligated to expeditiously remove or disable the allegedly infringing material and notify the subscriber of its actions in what is referred to as “notice and take down procedure.” The Purchase College DMCA infringement procedure is as follows:
The college also recommends that all students take theUniversity of Texas Copyright Crash Course or their Copyright Tutorial, or take other appropriate steps to further their understanding of copyright infringement. Counter Notice Under the DMCA, the college is obligated to inform you of certain requirements of that Act. You have the right under the Act to send a counter notice that you are not in violation or that the violation has ceased. That notice must be in the form required by the Act, and you are advised to seek legal counsel at your expense for appropriate advice on the form of any counter-notice. The specific statutory language is as follows: (17 USC 512(g)(3)): Contents of Counter-Notification: To be effective under this subsection, a counter notification must be a written communication provided to the service provider’s designated agent that includes substantially the following:
(A) A physical or electronic signature of the subscriber. The above is provided for your information only, not as advice, nor is it an attempt at stating the law or your responsibility. You should review the entire Act with your attorney.
You are responsible for any network device registered in your name (like a Wi-Fi hotspot). College Computer Network Users: if you lose access due to an alleged violation If you receive an official notice from the college of an alleged copyright violation and have had your network access restricted, please contact the Office of Student Affairs to find out how you can have your network access restored:
Office of the Vice President |
Example of a broken accordion, this table has an odd number of rows (three total):
| Privacy and confidentiality policy |
|
Purchase College is committed to protecting the privacy and confidentiality of information contained in the multiple databases and print files maintained by the college in the regular course of business. Personal information that is confidential in nature will be used only in accordance with Purchase College Information Security Program, Family Educational Rights and Privacy Act (FERPA), Health Insurance Portability and Accountability Act (HIPAA) regulations, and all applicable SUNY, state, and federal regulations. POLICY Employees at Purchase College by nature of their positions will gain access to private personal information about students, faculty, staff, alumni, and other constituents of the college. Employees are obligated to maintain the confidentiality of any such private personal information that is encountered. Purchase College expects all employees with access to personal information to deal with that information in a respectful and professional manner. As a matter of policy, the college restricts access to personal information to only those employees who have a legitimate “job-related reason” in the performance of their duties for gaining access. Access and release of any student educational records must be in accordance with FERPA regulations. Access and release of any health records must be in accordance with HIPAA regulations. Any personal information viewed or accessed by an employee through college systems or records is not to be shared or released to others unless there is a legally permissible purpose for doing so. In addition, in accordance with Section 203-d of the New York Labor Law, Purchase College will not:
Personal Identifying information (PII) is defined by NYS as including an employee’s Social Security number, financial account number and PIN, or driver’s license number. Access to PII will be restricted to those with a demonstrable need for access. Inappropriate disclosure of information pertaining to students, faculty, staff, and other college constituents may violate applicable law and is considered a violation of ethics and a breach of trust placed in employees by the college. Upon finding of a breach of this policy by an employee in a collective bargaining unit, the college may initiate disciplinary action pursuant to the applicable collective bargaining agreement, up to and including termination of employment. Employees who deal with confidential material on a regular basis will be required to sign a confidentiality statement and to complete annual information security training. Each campus manager will determine employees required to have access to PII who must receive training and sign confidentiality statements. GUIDELINES Employee, student, financial, and medical information contained within Purchase College information systems (electronic and physical files) and external SUNY systems is considered confidential. Access to information made confidential by law or campus practice is limited to those individuals (employees, consultants, adjunct professors, third-party vendors, etc.) whose position legitimately requires use of this information. The employees (Purchase College faculty, staff, student employees, and volunteers appointed by the college) understand that by virtue of their work for Purchase College they may have access to data that are confidential, and therefore understand they may not disclose such confidential data to any person or entity without appropriate authorization, subpoena, or court order. Examples of confidential PII information include the following:
In addition, FERPA regulations cover
In order to access confidential information, employees agree to adhere to the following guidelines:
|
|
PROCEDURES
|
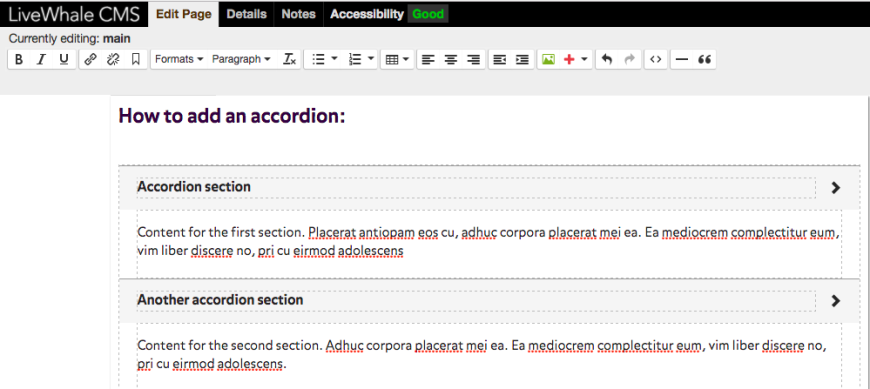
To add an accordion to your page:
- Edit page and click on the table button. Insert a table with only one column. Each section in the accordion needs two rows. You can always add more later.
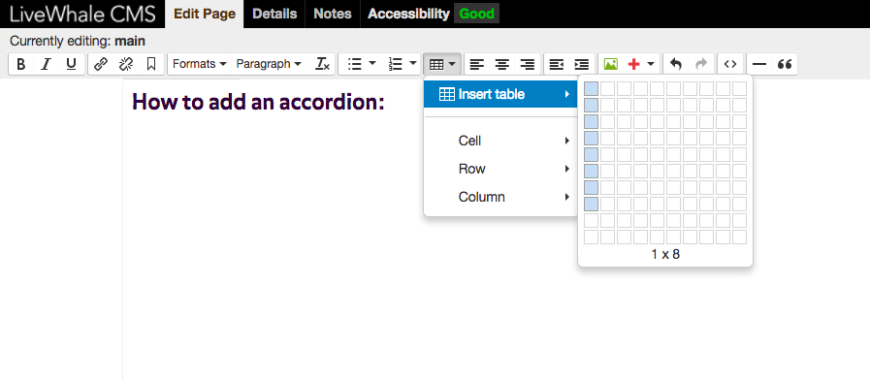
- Once you’ve inserted your table, select the table (if you’ve just inserted it, it should already be selected). Go to the Formats menu and select Accordion.
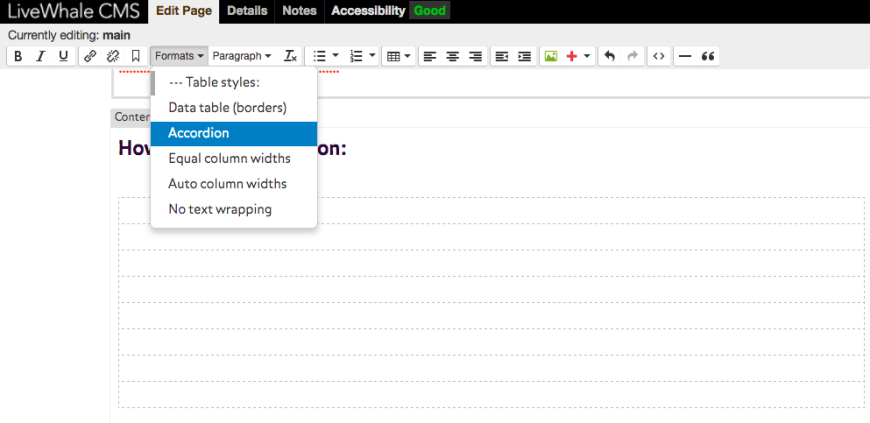
- Add titles and content to your accordion as shown. Once you save the page, the content of each section will be hidden.
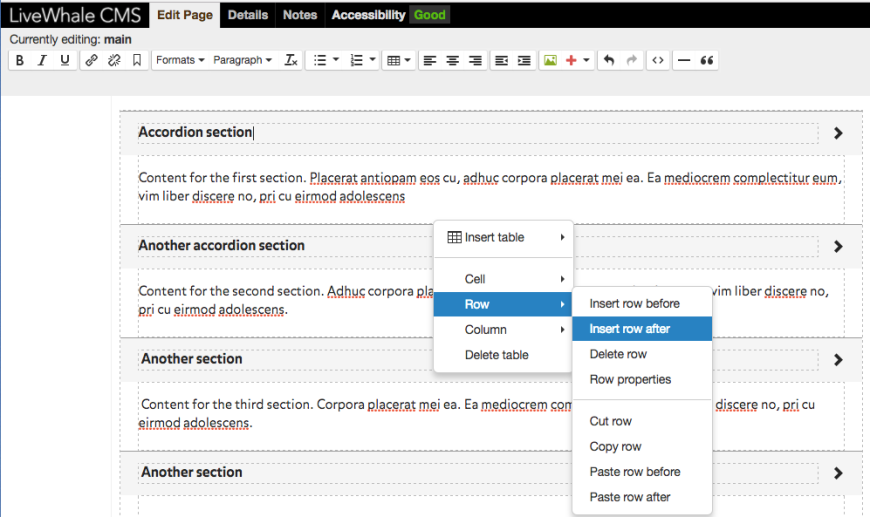
- To add more rows, right click on any row in the accordion and select insert row after or before.
Note: Please add two rows at a time, otherwise the styling and functionality breaks (one row is for the section title, one row is for the content).
- After saving, your accordion will display with all sections closed. You can click on each section to open it. Hit reload if it doesn’t work on the first attempt.